In light of the increasing adoption of cloud-native technologies, containers, and microservices-based architectures, the significance of log monitoring and management within organizations has risen dramatically. But, why?
It’s no news that cloud platforms like Amazon Web Services, Microsoft Azure, and Google Cloud Platform enable companies to digitally transform with unparalleled flexibility, efficiency, and scalability. However, their intricate architectures amplify the volume, speed, and diversity of log data generated.
This surge in log data complexity, compounded by the challenge of integrating it with metrics and traces for comprehensive observability, underscores the pressing need for innovative log monitoring and analysis approaches. No wonder, the global log management market is expected to grow by nearly 200% touching $4.1 billion by 2026.
This article dives deep into the world of log monitoring, emphasizing its significance in understanding complex cloud architectures. It will also explore best practices, practical use cases, and essential tools to effectively harness the operational and business insights locked within these logs.
What are logs?
In computing, a log is a record of events that have occurred, typically including a timestamp and event details. Logs are commonly used to troubleshoot issues, monitor system performance, and identify security concerns.
Software programs and systems generate log files containing information about the application, user device, time, IP address, and more. Various types of logs exist, such as application logs, system logs, and security logs.
Logs can be stored in various formats, including plain text files, databases, and specialized log management systems.
What is log monitoring?
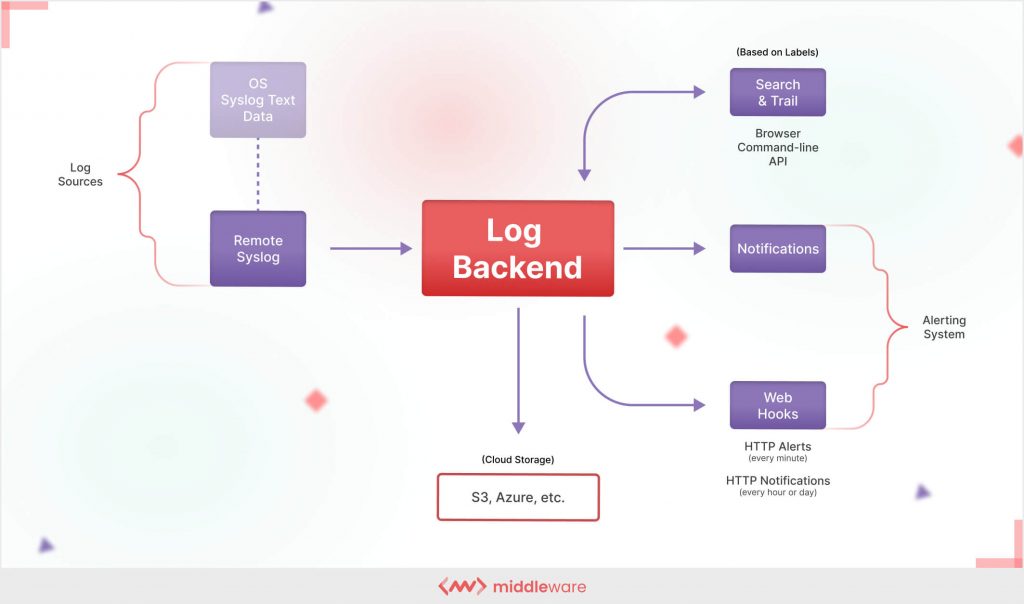
Log monitoring is the process of continuously monitoring logs to identify specific events or patterns that lead to a particular problem.
Typically, all network components, both software and hardware, generate logs during operation.
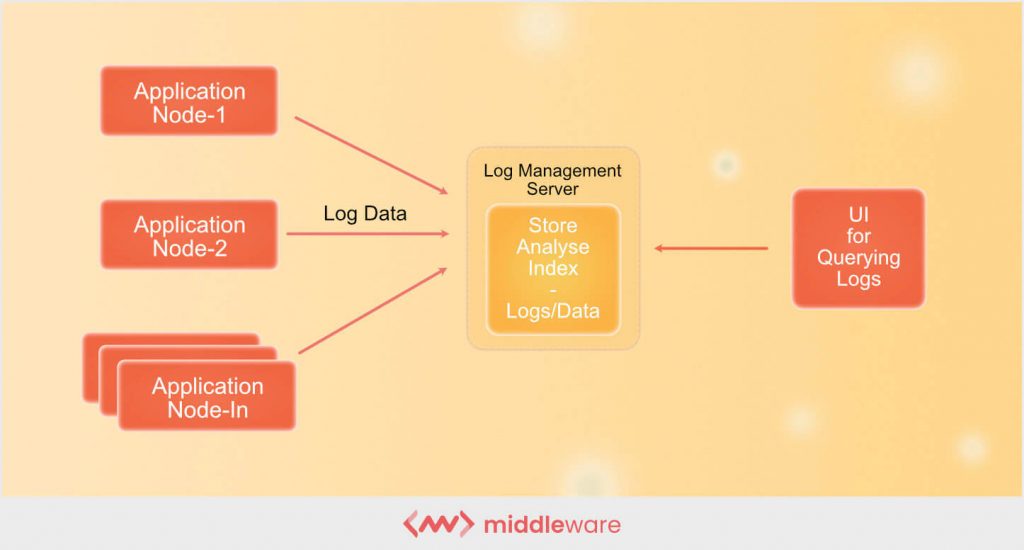
DevOps teams and developers collect and aggregate these log entries in a centralized location using log shipping, agents or any other methods. As most log entries come in different formats, developers then standardize the format to ensure consistency and readability.
Using monitoring tools, developers consistently evaluate incoming logs in real-time, aggregate log files and issue alerts or notifications for specific log messages and events.
On analyzing the data generated by these systems, they can identify anomalies within the system, and root causes of issues and troubleshoot them. Overall, log monitoring helps developers maintain system stability, detect security breaches, and trace system changes or updates.
As things stand, Log monitoring finds applications in diverse settings such as IT departments, web servers, and cloud-based systems.
Benefits of log monitoring
There are several benefits to log monitoring, including:
Enhanced compliance
Log monitoring aids businesses in complying with various laws and regulations, including GDPR, HIPAA, and PCI. It provides a cost-effective means to meet critical regulatory requirements.
Commonly tracked activities include:
- Login attempts
- Account management
- Directory access
- System activities
- Policy alterations
Rapid incident response and resolution
Log monitoring enables quick incident detection and resolution, preventing impact on end users.
Heightened security
Monitoring logs identify code vulnerabilities, enhancing program performance by:
- Identifying weak performance areas
- Debugging and evaluating application health
- Detecting installation and runtime issues
Improved team performance
Log monitoring optimizes system performance by identifying bottlenecks and ineffective configurations. It involves:
- Real-time health monitoring
- Identifying performance or configuration problems
- Monitoring operational goals and SLAs
Improved team collaboration
Unified log monitoring benefits cloud operators and architects, promoting:
- Rapid event response and issue identification
- Effective collaboration among stakeholders
Greater visibility
Teams can enhance their IT automation efforts and execute processes and responses more precisely by gaining visibility into essential system metrics.
Log monitoring use cases
At the heart of modern IT operations, log monitoring provides valuable insights into system health and performance.
Here, we explore practical use cases that highlight its essential role in boosting security, ensuring compliance, and optimizing application performance:
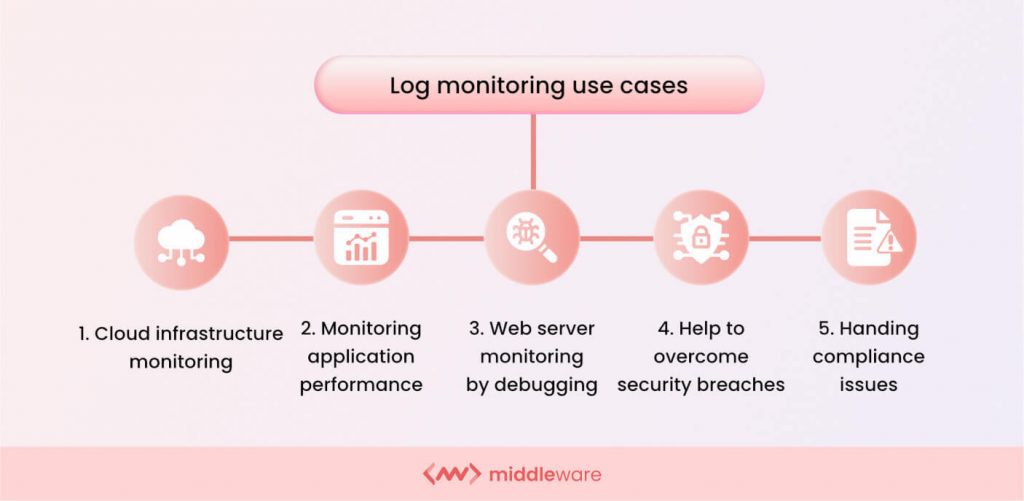
Cloud infrastructure monitoring
It inspects, monitors, and oversees the operational processes of an IT infrastructure. Manual or automated management methods verify the performance and availability of websites, servers, applications, and other cloud infrastructure components.
This continual evaluation of resource utilization, server response durations, and velocity reveals potential vulnerabilities before they manifest.
Leveraging cloud-based resources efficiently is achievable through cloud log monitoring. Modern log monitoring tools can gather diverse logs and data from various origins.
It can trace hosts, virtual machines, platforms, and third-party resource integration, networks, and device information.
Here are a few benefits of cloud monitoring:
- Scaling for increasing activity is simple and effective in businesses of all sizes.
- The host maintains relevant tools and hardware.
- Tools may be used on various devices, such as smartphones, tablets, and desktop computers, allowing your company to monitor apps from anywhere.
- Infrastructure and settings are already in place, making installation straightforward.
Monitoring application performance
Log monitoring tracks application performance and detects issues affecting user experience. Businesses often employ distributed tracing and monitoring (metrics) to oversee their applications.
Logs are the preferred source for connecting the dots across an application stack, facilitating troubleshooting and program debugging.
- Helps spot issues before they affect consumers.
- Monitors app components like servers, databases, and more.
- Offers alerts and a dashboard to remove application bottlenecks.
Web server monitoring by debugging
Log monitoring enhances user experience when your company website or application is hosted on web servers like Apache or IIS. Server logs oversee traffic volume, service problems, and failures.
Developers benefit from log monitoring to pinpoint and resolve application issues by tracking user or process actions. Keeping a watchful eye on web server logs aids in enhancing online applications, identifying traffic surges, and expediting issue resolution.
Overcome security breaches
Log monitoring identifies security breaches like unauthorized system access or data theft and alerts the relevant parties.
Resolving compliance issues
Log monitoring aids organizations in ensuring compliance with regulations like HIPAA or GDPR. It tracks access to sensitive data and sends alerts for unauthorized access attempts.
Log monitoring best practices
Here are the best practices for log monitoring:
Use of structured logging
When analyzing log files, structured methods for logging are recommended. They make examining logs easier than dealing with unstructured text data, which can be time-consuming and error-prone.
Add labels or unique identifications
Tagging logs is helpful for troubleshooting and debugging, making it easier to segment and filter records. Unique string values can be used to narrow down searches, which is especially crucial in container systems.
Real-time monitoring
Real-time monitoring helps promptly resolve issues in a live environment. It enables the detection and resolution of problems as they arise, preventing them from becoming major issues.
Set up alerts
Constantly monitoring everything can be challenging, so it’s important to establish baselines for monitoring metrics and configure alerts for deviations from these baselines. This helps IT staff stay on top of their environment.
Enhance log retention policies
Define specific log retention rules based on your organization’s needs and compliance requirements. Keeping logs for extended periods may sometimes be necessary to comply with data protection laws or for long-term performance and activity analysis.
Organize, aggregate and customize log data
Collect log data from various IT infrastructure sources into a centralized location for effective data analysis. Use customization features to identify and resolve specific errors or debug logs quickly.
Log monitoring challenges
While log monitoring remains essential for IT operations, Translating incoming logs and data into helpful use cases can be challenging. Listed below are the set of hurdles you can expect while monitoring logs:
Increased log volume and formats
The issues with log monitoring surface at the very first step and are two fold.
The first issue revolves around the volume of data that continues to increase As systems and applications grow, the data they produce grow simultaneously – which is obvious.
However, the systems that process and analyze this data don’t really change, making it extremely challenging to gather insights. The second issue lies the diverse log formats that different applications and systems use.
While it’s pretty easy to collect, standardize, and analyze small sets of log data, large data sets require much more due diligence and efforts to consolidate and interpret.
Data silos
Unlike most present-day startups that were born digital, companies that have been around for more than a decade deal with many legacy systems which generate logs in silos.
These data silos restrict the ability to integrate and correlate log data from different sources, increasing both time and effort to achieve a unified view of the entire system.
IT complexity
It’s no news that modern IT environments are inherently complex. With the increasing adoption cloud technology, microservices architecture, and AI, it’s safe to say that the complexity will compound as the days the pass.
Though these advancements offer immense business value, they make it difficult to understand the relationships between different components, hindering our ability to identify, troubleshoot, and predict issues.
Data storage cost
Though important from a monitoring perspective, storing large volumes of data can be expensive, especially as the data retention periods increase. As per recent stats, cloud data storage costs are doubling every four years. Meaning, companies need to find a balance between the need for historical data and storage costs.
How to select the best log monitoring tool?
Choosing the optimal log monitoring tools involves considering specific business needs related to log volume, scalability, compliance, and log retention. Here are the key considerations:
Privacy and compliance
Privacy compliance refers to an organization’s requirement to handle sensitive data with care as it is received on a daily basis. This procedure enables businesses to meet commercial and regulatory demands for data preservation and management.
HIPAA imposes rigorous standards for log management and audits.
- What modifications or exchanges involve confidential data?
- Who accessed specific data and when?
- Employee logins
- Software and security updates
- Both system and user activities
- Unusual usage patterns
Log volume and retention
Assess your daily log volume, accounting for data spikes and anomalies. Determine whether you need live tailing and real-time debugging, whether logs must be retained for compliance, and the desired data retention duration.
Cost and scalability
Cost plays a significant role in decision-making. A pay-per-gig approach offers adaptability and smart utilization of a logging platform. Depending on your product, your log processing might shift from a few thousand logs per day to millions overnight. Use this checklist to calculate operating costs and identify desired features from a log management platform.
- Free trial availability
- Presence of a free plan with live tailing
- Tracking log volume storage retention costs
- User limits and solutions for exceeding them
- Features provided across all plans
Top 9 log monitoring tools
Middleware
Middleware is a full-stack observability platform that gives you complete transparency and analysis of your entire tech stack. This log monitoring tool offers a cost-effective approach to centralized log management.
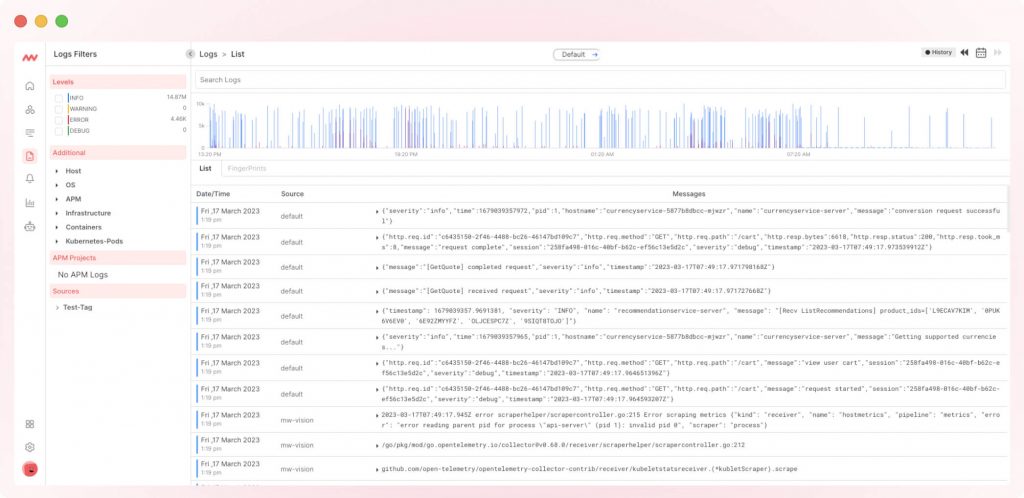
Middleware enables users to quickly find real-time solutions and optimize resources by identifying root causes.
- Summarize log activity in a single interactive dashboard to spot potential issues as they pop up.
- Create an efficient platform to monitor and analyze logs from several sources.
- Manage logs that fit into your organizational structure, regardless of the role.
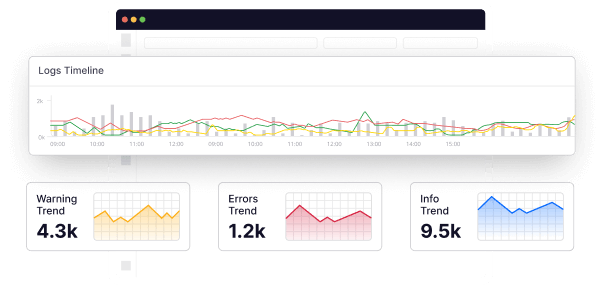
- Get search results in seconds with all your data on one platform. Even further, select logs in a particular timeline.
- Investigate potential threats using alerts when an issue occurs.
- Diagnose issues in real-time.
- Supports various open-source log data frameworks.
Pricing
- Free with limited usage
- Almost 5x less cost than other competitors
- Custom pricing for enterprise edition
- Best price in the segment
Dynatrace
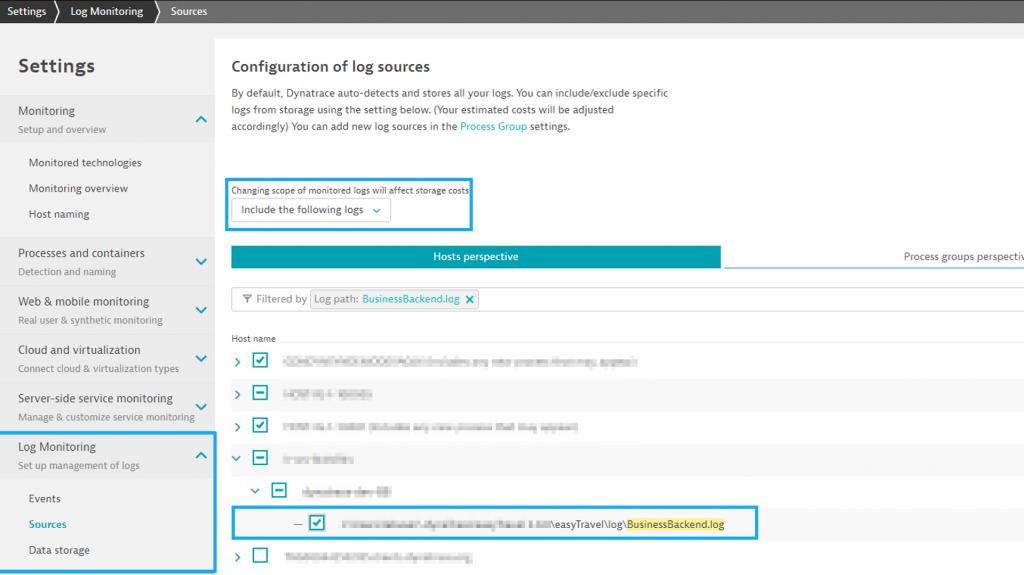
For better AI-powered full-stack observability that produces results and continuous automation, Dynatrace combines logs with other data sources such as metrics, traces, and actual user data, all in context with dependency mapping.
- Enterprise-scale Dynatrace automatically gathers log and event data from various technologies in hybrid and multi-cloud settings.
- Supports multi-cloud systems natively, including Red Hat OpenShift, Microsoft Azure, Google Cloud Platform, and AWS.
- Support various open-source log data frameworks.
Pricing
- Basic Starts from $11 per month
- Full stack monitoring – 74$ Per month
- Pay as you go for the enterprise edition
Newrelic
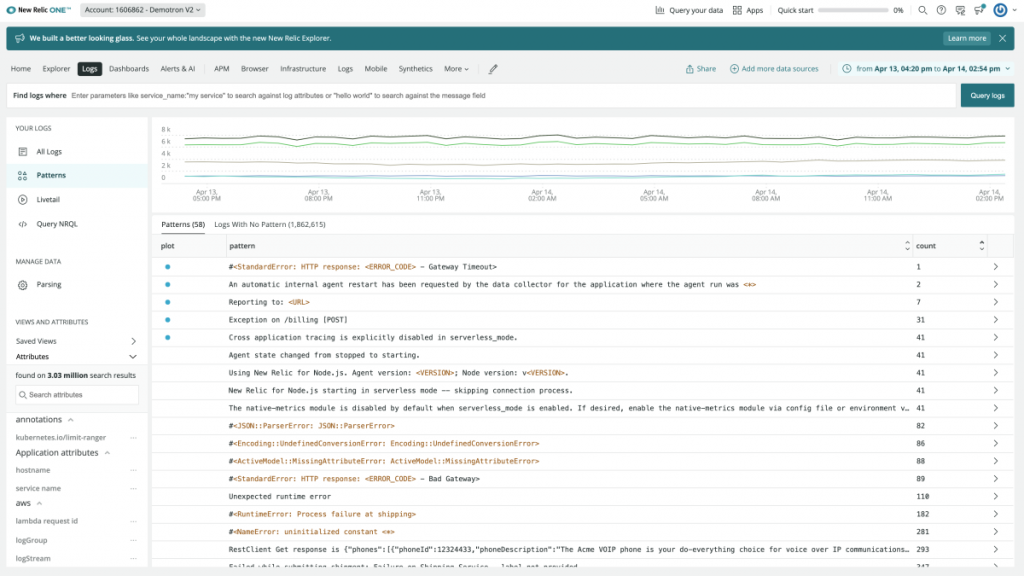
New Relic offers a single platform for all telemetry data, including metrics, events, logs, and traces, along with analytical tools for quick problem-solving. Discover the “why” by looking past the “what.”
- Log management in New Relic automatically adjusts to the volume you utilize. Rates for data and users won’t rise. As a result, you will constantly be aware of the price.
- Get search results in seconds with all your data on one platform. After that, utilize data partitioning to divide the data any way you choose.
- Ingest text-based data from anywhere with ease. Pick the New Relic log forwarder that works best in your environment, then deploy it.
Pricing
- Free with limited features
- Custom-based pricing for Pro and Enterprise edition
Datadog
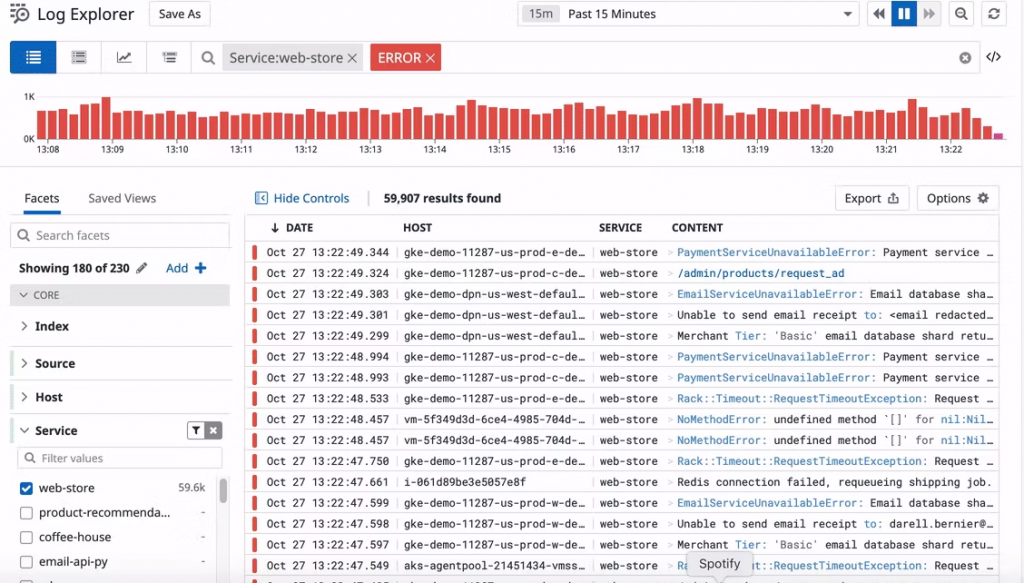
It is a SaaS-based software for monitoring cloud applications. With tools like Datadog, keep an eye on serverless operations, system activities, Windows and Linux hosts, and cloud-based software. It may be used to manage logs, investigate metrics, and display data, among other things.
- Create shareable, real-time dashboards that include metrics and distributed traces, log visualization, and monitoring.
- Receive notifications when you go beyond user-defined log monitoring thresholds for a certain amount of time to spot problems like build job notifications or code exception failures.
- Utilize 500+ technology integrations to create unique pipelines that rapidly process and enrich logs.
- Free
- Pro – $15
- Enterprise- $23
Sentry
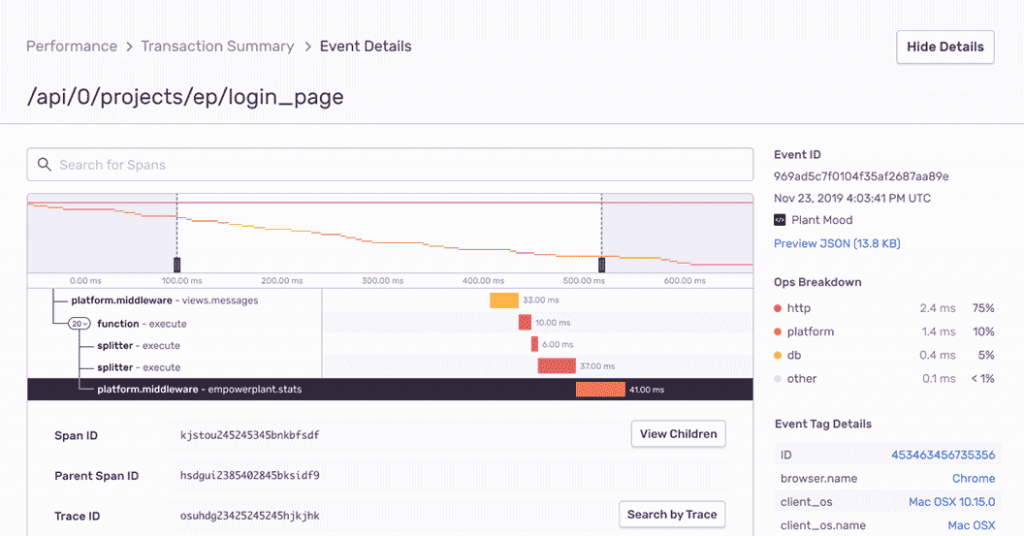
Sentry is an event-logging platform whose primary goal is to gather and record exceptions. It was first designed at DISQUS in early 2010 to address the issue of exception logging in a Django application.
Since then, Sentry has expanded to support a variety of well-known programming languages and operating systems, including Python, PHP, Java, Ruby, and Node.
- With stack traces, Sentry improves application performance monitoring.
- Examine the entire end-to-end distributed trace to identify the precise, underperforming API call and reveal any associated problems.
- Whether you’re using JavaScript, PHP, or something in between, Releases provide visibility into which mistakes were fixed and which were made worse.
Pricing
- Free with limited features
- Team – $26/mo
- Business – $80/mo
- Custom pricing for enterprise edition
Sentry is a good tool, but Middleware is better. Know why!
Splunk
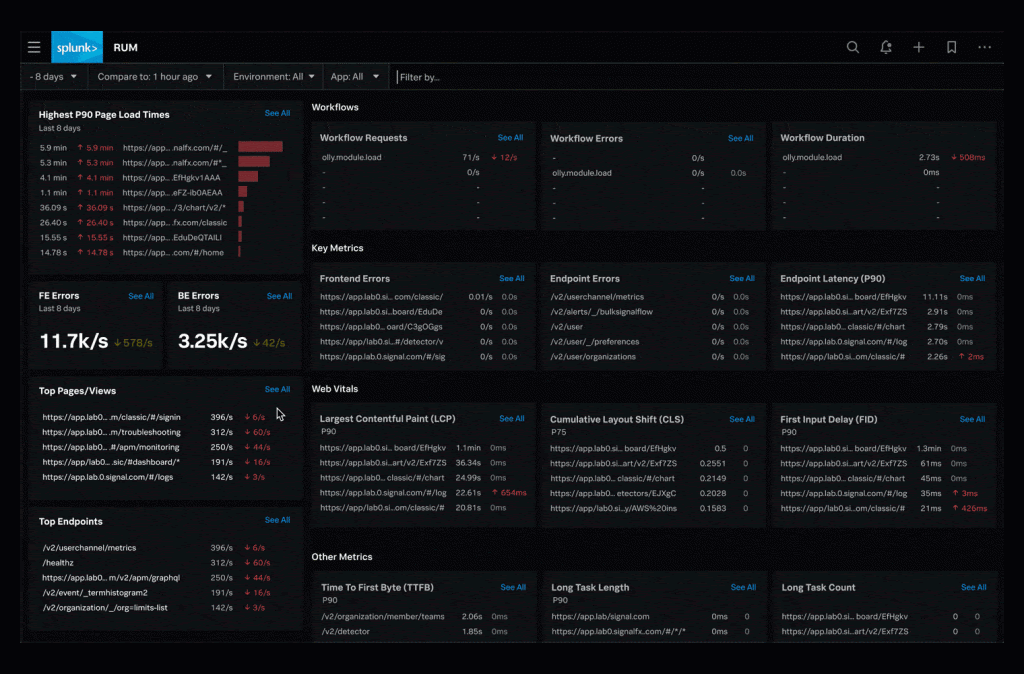
Splunk is designed to enable the process of indexing and interpreting logs of any kind, including complex application logs and advanced unstructured logs, using a multi-line approach.
- Maintain your flexibility and agility to generate high performance and succeed in the cloud.
- System for monitoring and alerting users to significant activities and events.
- Real-time data search and analysis with a flexible user interface.
Pricing
- Free- 500MB/per day
- 185$+ for the cloud version.
- 2000$+ for the enterprise edition.
LogDNA/ Mezmo
Mezmo’s intuitive log management platform unleashes the potential of log data. Data must be ingested, normalized, and routed to DevOps, IT Ops, and development teams so they can respond quickly and effectively.
- You can comprehend and control data spikes using quotas and index rate alerting.
- Receive notifications for specific searches, correlations, and storage criteria.
- Users can arrange data to make it more usable with the help of auto and custom parsing and enrichment.
Pricing
- Free with limited features
- Professional – $0.80/GB
- Enterprise – CUSTOM
GoAccess
GoAccess is a real-time log analyzer program that can be used with a browser or a Unix terminal. It offers an immediate logging environment where information can be viewed milliseconds after it has been saved on the server.
- Completely Real Time
- Application Response Time Monitoring
- Incremental Log Processing
- Minimal configuration needed
Pricing
- Open-source
Graylog
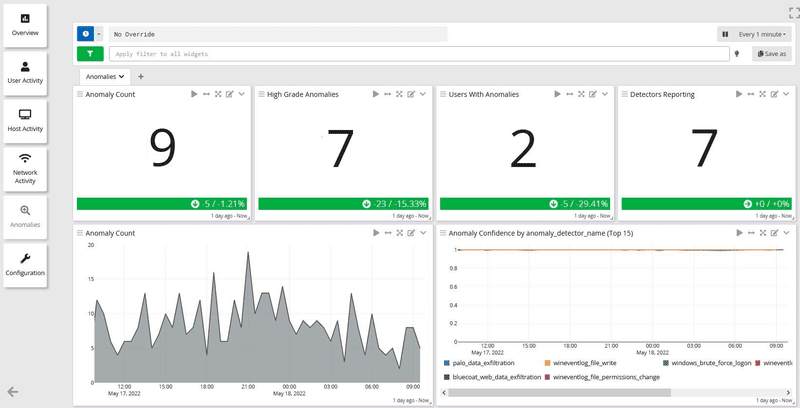
Graylog enables you to adhere to compliance regulations and aids in determining the root cause of any specific mistake or issue your apps may be encountering. In addition, large and complicated IT infrastructures may be monitored with the help of this powerful technology.
- Personalized dashboards for query and log data visual output.
- Team members have access to centralized management.
- Individualized permission control for users and their roles.
- Personalized triggers and notifications to track any data problems.
Pricing
- Open-source
- Enterprise: $6,000/year
How Middleware unlocks the value of log monitoring
Log monitoring is crucial for determining your system’s current performance, maintaining its functionality, and enhancing its effectiveness. You can monitor log events accurately and optimize log monitoring using log monitoring software.
Although log monitoring is essential for enhancing your comprehension of performance, facilitating informed decisions, and optimizing functionality, it presents a formidable task. Efficiently, accurately, and reliably monitoring thousands of real-time logs can prove challenging.
The Middleware platform simplifies log monitoring, making it reliable and cost-effective. Using it, you can effortlessly monitor and analyze logs from infrastructure and front/back-end systems in a unified location. You gain enhanced control over your infrastructure’s health and performance through a centralized dashboard, offering improved reliability, scalability, support, and visualization.
The ability to quickly locate, debug, and resolve issues is crucial to log monitoring. Middleware’s advanced filter options enable faster log retrieval, and you can save these filters to set your preferred logs as the default view.
Middleware offers an improved timeline for specific logs, aiding in issue pattern identification. Additionally, log details allow you to link logs to their sources, assisting in root cause analysis.
Sign up for free to get real-time observability of logs and its potential to elevate your application’s security, compliance, and performance.
FAQs
What is log monitoring?
Log monitoring is the method of analyzing system logs in real-time to identify and resolve issues. It is essential for maintaining system and application availability, security, and reliability.
This process includes detecting anomalies, pinpointing security threats, and monitoring performance metrics using log analysis tools.
Why is monitoring log important?
Log monitoring is crucial in managing IT operations and enables organizations to enhance system availability, security, and performance while minimizing downtime and business disruptions.
It is essential for troubleshooting, performance optimization, security threat detection, compliance adherence, and trend identification to predict and prevent future issues.
What are the three different kinds of logs?
- Availability logs: Used to monitor system performance, uptime, and availability.
- Resource Logs: These logs contain information on connectivity issues and capacity limits.
- Threat logs: These logs contain information about system, file, or application traffic that matches a firewall’s predefined security profile.
What are the best log monitoring tools?
Many log monitoring tools are available in the market, and the right one for you depends on your specific needs and preferences. Some popular options include Datadog, Middleware, Elastic, Splunk, and Graylog.
![What Is Log Monitoring? A Detailed Guide [Updated]](https://middleware.io/wp-content/uploads/2022/08/log-monitoring.jpg)